Warning: Much of the topics covered below will be too much for 99% of people, including myself. However, it is useful and interesting to be aware of what's possible and apply whichever techniques you would like.
How to stay as safe as the best
Not to make you feel bad after all this hard work, but even with everything we’ve done in the previous lessons, you are not un-hackable. If you feel paranoia and fear that you are being specifically targeted (like our friend Edward Snowden) then you need to take far more steps, and even that may not be enough. For instance, Mr. Snowden drapes a pillowcase over his head when entering passwords, in order to avoid them being compromised by spying eyes or cameras.
This lesson is by no means intended to guarantee you are invincible and hack-proof, it’s more of a thought experiment on thinking more like a ‘Snowden’.
Targeted Attacks
If you believe you’re a high value target (journalist, celebrity, high net-worth, powerful, an enemy in the government's eyes like a whistleblower) then hackers are incentivized to push harder (and will invest more resources and money to hack you). For this reason it’s extremely hard to stay safe. You effectively have to be a crypto-nerd techie or hire a specialized security team. Even with all this, if bad people get you in a room, they will get your information.
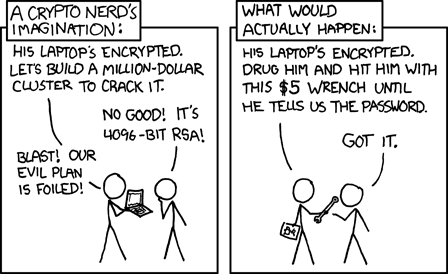
If you are this sort of target, you have far more to worry about, like kidnapping, physical attack, blackmail, and you also likely have money to pay for protection. This is wayyyy out of scope of this site, so please go hire a professional firm, like Gavin de Becker and Associates, who advise many of the world’s most prominent media figures, corporations, and law enforcement agencies on predicting violence, and also serves regular citizens who are victims of domestic abuse and stalking.
The Easiest Defense — Reduce, Reduce, Reduce
Follow this simple formula:
+
less data
+
less passwords
+
less personal information
=
fewer vectors for attacks.
When posting publicly or entering information online, take a moment to think about what personal information the service actually needs and provide the minimum. Same goes for posting online, how much do you really need to share with everyone on your social media or the public. Some obvious cases of where people provide too much information or overshare:
- providing extra information - birthdates, addresses, school names, children's names, places of work
- photos including private info - think cars with license plates, your home, photos of your children, or even documents with addresses or any identifiable info
- photos with GPS information - most devices attach location information to photos you take, you should learn to remove it yourself before uploading
- locations of your home or work - includes posting workouts that start and end at home. The US government even screwed this one up and gave away the location of a secret military base in Afghanistan. Strava offers a privacy zone feature where you add a bounding box so it won't display the starts and ends of your map publicly but still allows you to share.

Pseudonymity and Doxxing
Using a pseudonym simply means using a fake name. You've probably seen a friend that uses a fake name on their Facebook or Instagram account. This is a good practice because it makes it more difficult for malicious actors to connect your online presence with your real identity (and therefore your real bank account, social insurance number, address and so on).
Doxxing, or being doxxed is when someone has their private information leaked online without their consent, or in the case of someone acting under a pseudonym, having that publicly connected back to their real name.
The strength of your pseudonym is in how difficult it is for someone to doxx you. For social media it is likely good enough to use a fake last name to avoid unwanted people from finding you. The pseudonyms are weak, due to the nature of social media. You are interacting with many friends that know your real identity and could doxx you. This can even happen unintentionally by using your real name when commenting on a photo or a post.
If you are a whistleblower, you will probably want a full pseudonym, that has absolutely no connections back to your real identity. This means a using an identity that nobody you don't absolutely trust knows is one. It means using a different email to sign up, providing distinct information for every part of the signup. It can even extend to adapting your writing style, as their are machine learning algorithms intended to notice patterns in word usage and grammar styles.
Truly Private Browsing with Tor
Sometimes you want to be truly private online. This is very difficult, inconvenient and slow, but in the end possible to achieve.
You may have heard of the Silk Road or the Dark Web, which made Tor (the onion router) famous. Aside from its obvious illegal use cases, there are many legitimate reasons to use this approach for true anonymity online, including avoiding detection by oppressive regimes. Using Tor to browse the internet is sort of like having a VPN on steroids, bouncing your data across several random inter-connected devices in a network around the world to encrypt your data.
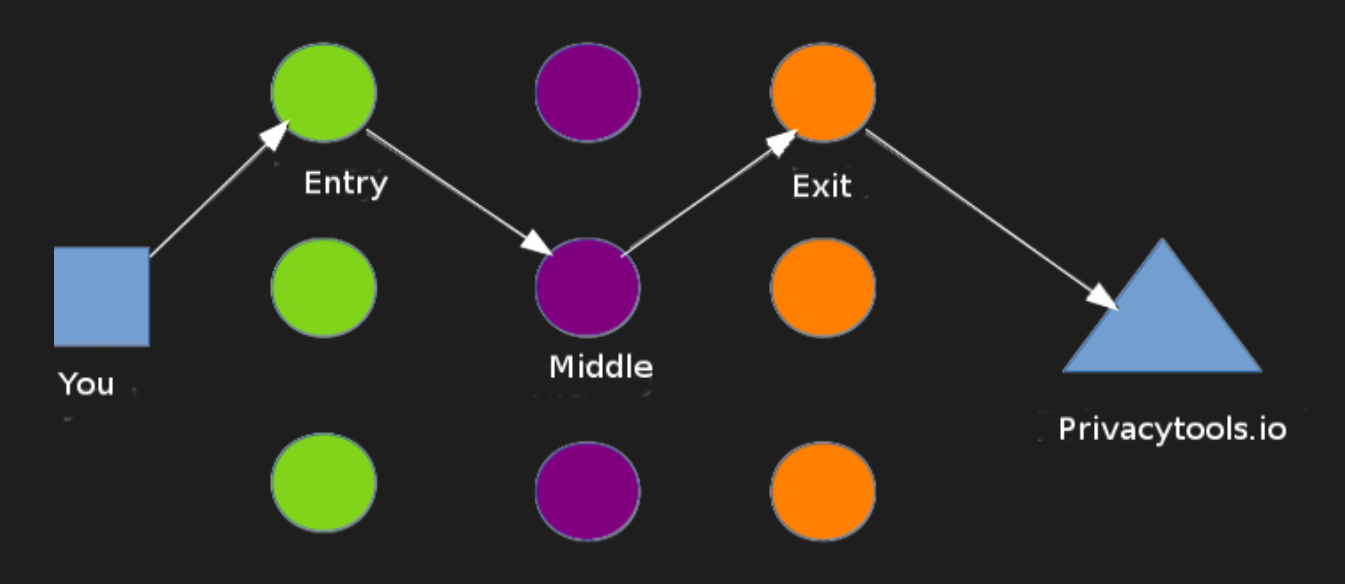
Using Tor alone is not enough. You must layer many other techniques such as:
- never accessing the internet from home or work
- obfuscating your information in a way that never ties back to your real identity
- using a VPN over Tor
- using encrypted chat like Signal
- using a Tor-specific operating system like Tails or Whonix
You have to be smarter than a Hollywood spy to do this right. If you do, remember that a single mistake can make all the privacy disappear in a snap. Ross Ulbricht (the former operator of the Silk Road, who went by the pseudonym Dread Pirate Roberts) thought he was smart and careful but was caught when someone discovered his Silk Road username used on an old forum with his real email address. He is now serving double life + 40 years without possibility of parole, for money laundering, computer hacking and conspiracy to traffic narcotics.
This approach is not for the faint of heart, and make sure you have a really good reason or it's honestly not worth all the hype.
Protective Actions
Here are some other protective actions you can take:
Airgapping: This is when you have a computer that is not connected to the internet in any way. If you have a high-value bitcoin wallet, or extremely senstitive documents, you may want to put them on an airgapped device and store them in a safe. Just make sure you have backups (also airgapped) elsewhere.
Erasing data: If you are going into a sensitive area and want to protect your data, you can erase your devices. This would protect you against your devices being read at a border crossing. The downside is the inconvenience of restoring your device on the other side of the border. Also, ensure that whatever method you use to erase your device does a full erase, not one that can be restored.
Mr. Robot
For a really fun dive into the world of hackers I highly recommend the TV show Mr. Robot by Sam Esmail. Beyond the gripping story, beautiful cinematography and fantastic acting, the creators took great pains to make the attacks and protections as realistic as possible.

Useful Resources
To end off, here are some useful links if you'd like to dive deeper.
- How to Talk to Your Family About Digital Security [EFF]
- Encryption and tools to protect against global mass surveillance [Privacy Tools]
- Enterprise Cybersecurity: How to Build a Successful Cyberdefense Program Against Advanced Threats [Book]
- Password Cracking [Computerphile]
- What To Know About Identity Theft [FTC]
- Facts + Statistics: Identity theft and cybercrime [III]
- Extreme Security Measures [Wired Magazine - behind a paywall]
- The Day-In-The-Life of a Hacked Smartphone video [Privoro]
- Anonymity, pseudonymity, and the agency of online identity [FirstMonday]
- The Trend Towards Online Pseudonymity [GlobalSign]
Thank you!
We just wanted to thank you for sticking with us through this long course! Don't forget to go back and do any lessons you skipped. And please let your friends know about us!
Back to the Lesson Plan
Header image credit: Edward Snowden wallpaper
